2026.1 Release Notes
For a list of release dates and Sisense's end of support schedule, see Sisense Version Release and Support Schedule.
For information about the Sisense gradual rollout process, as well as an explanation of how the versions and release notes relate to content added during the rollout, see Sisense Gradual Rollout Process.
Versions Documented in these Release Notes
Regarding Salesforce Security Updates to the "Use Any API Client" Permission:
-
For customers using Sisense connections to Salesforce, it is important to note a significant Salesforce change and steps that you may have to take for continued correct functionality. See Salesforce “Use Any API Client” Permission Changes: Sisense Impact & Migration Guide.
Regarding Upgrading:
-
Version L2025.4 Service Pack 1 contains an important fix. Therefore, it is strongly recommended to upgrade to SP1 (or newer, when available).
-
Customers currently running Sisense versions older than L2025.2.0.249 cannot directly upgrade to versions L2025.3 or newer. You must first upgrade your Sisense installation to version L2025.2.0.249 or L2025.2.0.496. Only after completing this intermediate upgrade can you proceed to version L2025.3 or newer. This important change is due to Sisense upgrading to MongoDB 8 starting from Sisense version L2025.3.
-
To download the latest Sisense version, or to upgrade to an older version, see that version’s Release Notes and contact your Sisense Customer Success Manager for the version package.
-
To upgrade to this version of Sisense:
-
Read the Release Notes of all the versions following your current version, up to and including the version to which you are upgrading.
-
Run a system backup before upgrading. See Backing up and Restoring Sisense.
-
Follow the upgrade procedure in Upgrading Sisense.
-
Privacy and Security Information
This release contains several security related updates. We highly recommend upgrading to this latest release to take advantage of any security-related updates and benefit from the Sisense support and warranty. In addition, Sisense strongly recommends regularly testing and auditing your environment after upgrading, and periodically during your subscription term, to ensure all privacy and security settings remain in place.
Customers are responsible for controlling and monitoring your environments and are therefore in the best position to ensure the correct security settings are in place for how you use Sisense products.
Due to the complexity of Sisense products, we strongly suggest that all customers ensure that you understand how all of the privacy and security settings within Sisense work.
If you use Sisense to store/process sensitive data, it is your responsibility to review and test your implementation to ensure you are not inadvertently sharing data with unauthorized third parties. For more information on data security rules, see Data Access Security.
BREAKING CHANGES - WARNING!
The following is a cumulative list of potentially breaking changes from approximately the past 12 months, and may also include warnings about upcoming changes:
The Report Manager URL has now changed from /reportManager/main.html#/reports to /app/report-manager#/reports. This is necessary only for when embedding the Report Manager directly by URL.
2026.1.0 Release Overview
Release 2026.1.0 provides a number of new features, improvements, and fixes to Sisense for Linux.
What's New
The following table lists the high-level impact (or potential impact, if any) of new features, and how to handle it if upgrading to version 2026.1.0 or newer. Continue reading the Release Notes below the table for a detailed explanation of these features, as well as improvements and fixes.
| Feature | Issues and Actions to Consider |
|---|---|
|
|
|
| Two-Factor Authentication | Currently in Beta. See the complete documentation here. |
MCP Server
The Sisense MCP Server provides integration with the Sisense analytics platform. This server enables LLMs and AI assistants to interact with Sisense data models, explore data sources, and create charts using natural language prompts.
With the MCP Server, you can:
-
List all available data sources in your Sisense instance
-
Explore fields and structure of any data source
-
Create charts and visualizations from natural language prompts
-
Access chart screenshots via HTTP endpoints
For more information, see the Quick Start Guide and the Readme.
Two-Factor Authentication
This release introduces email-based Two-Factor Authentication (2FA) for Sisense native users as a Beta feature.
When 2FA is enabled, before they can access Sisense, native users must provide:
-
Their Sisense username and password, and
-
A one-time password (OTP) sent to their registered email address
This significantly reduces the risk of unauthorized access due to leaked or reused credentials.
2FA is controlled at two levels:
-
Deployment-wide (system) feature toggle - Enables or disables 2FA on the entire deployment.
-
Per-user configuration – Controls whether a specific native user is required to complete 2FA at login.
The default values are false/off for both of the controls during this Beta stage.
The following is the login flow for a native user with Require Two-Factor Authentication: true when the global feature toggle is ON:
-
Enter your username and password on the standard Sisense login page.
-
After successful credential validation, Sisense displays a 2FA code screen.
-
Sisense generates a time-limited OTP and sends it to your registered email.
-
-
Enter the OTP on the 2FA screen.
-
If the OTP is valid and not expired, you are logged in.
-
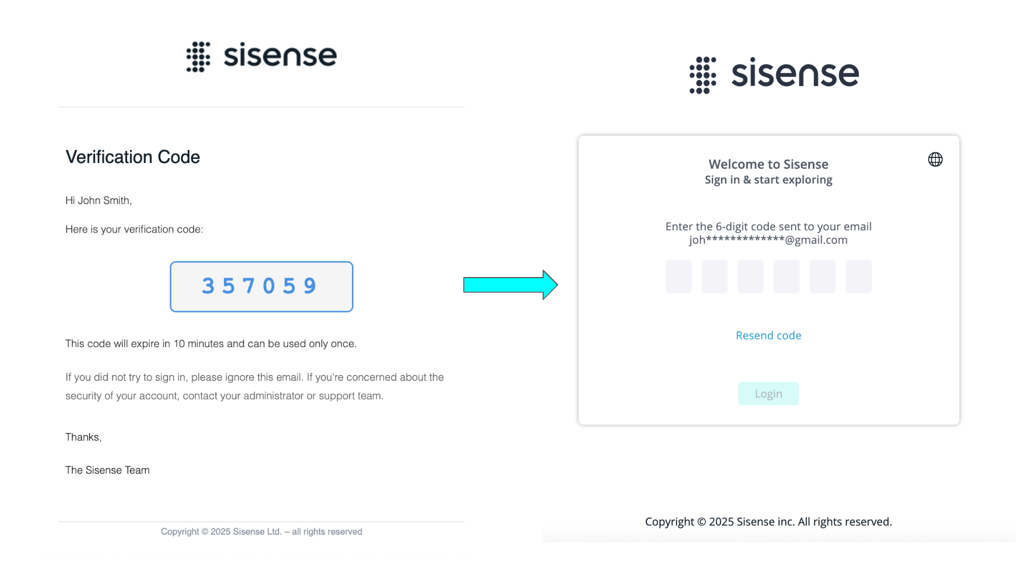
For more information, see Email-Based Two-Factor Authentication (2FA) for Sisense Native Users (Beta).
What's Improved
Add-Ons
-
Previously, the metadata add-on that displays column and table names in a language different from the database was not compatible with the AE (Analytical Engine), causing the system to default to the OT (Original Translator). This has now been fixed and the AE fully supports the metadata add-on.
Build To Destination (B2D)
-
Build to Destination connections are now fully isolated from the regular data source connections managed via Connection Management. From now on, B2D connections can only be created or managed using B2D API endpoints.
Compose SDK Mode
-
Calendar heatmap and Tabber widgets are now compatible with and supported in Compose SDK mode.
-
The Compose SDK Mode feature is now enabled by default.
Connectors
-
Previously, the Snowflake default authentication method was based on a PEM key which was stored unencrypted in the server filesystem. To enhance security Sisense now allows and defaults to authentication based on “private key content” which is encrypted and inaccessible to internal users once its saved.
-
A new option was added for the Snowflake connector to paste the content of the private key instead of uploading the file into the server.
-
The Databricks driver has been updated to version 3.0.1.
-
The Singlestore-jdbc (MemSQL) driver has been upgraded to version 1.2.8.
Infra
-
Sisense now supports Red Hat Enterprise Linux (RHEL) 10.
Note: If you are running Red Hat 10 and are offline, you must install
kernel-modules-extrabefore running the Sisense installation:sudo dnf install kernel-modules-extra-$(uname -r) -y
Sisense Intelligence
-
Sisense now supports GPT-4.1.
-
There is a new API endpoint for testing LLM connectivity by model ID:
-
Previous endpoint:
POST v2/ai/llm/test. The contract was changed (see the REST API description); this method is being deprecated and will be removed in a future release. It is recommended that you migrate to the new method (GET - see below). -
New endpoint:
GET v2/ai/llm/{modelId}/test. This is a new public API method to check BYOK configuration by ID (you can get the list of added configurations viaGET v2/ai/llm/models).
-
Sisense Version Naming and Schedule
Sisense version names and the release frequency is now as follows:
-
Major releases > released quarterly
-
Service packs > released monthly
-
Patches > released as needed on a case by case basis - e.g., fix to the released version, adjustment required by external changes, etc.
The letter “L” will no longer precede the version number.
The format is now: YEAR.QUARTER.SERVICE_PACK-PATCH
Examples:
-
2026.1.0 > first major release of 2026
-
2026.2.1 > first service pack for the second major release of 2026
-
2026.1.0-a > first patch to the first major release of 2026
What's Fixed
Add-ons
-
Previously, when using Jump to Destination (JTD) in Shared Mode, the target dashboard filters did not refresh based on the selected widget. This has now been fixed and JTD works as expected in Shared Mode.
-
Previously, filter relationships were not fully supported by Jump to Dashboard - some filters were not passed as expected. This has now been fixed and the filter relationships are transferred to the target dashboard, with all filters aligned. Note that if
mergeTargetDashboardFiltersis true andfilterRelationsexists, all filters passed to the target dashboard will be converted to single-level (non-cascading) filters. -
Previously, using primary filters in conjunction with JTD sometimes either caused console errors, allowed selection of excluded items, or caused filters to appear as both primary and regular filters. The filter intersection logic between source and target dashboards has been fixed so that primary and secondary filters now retain their correct roles and values when JTD is used.
-
Previously, in some instances, the plugins pod entered a CrashLoopBackOff state following an upgrade to an early build of version 2026.1.0, impacting plugin functionality and customer environments. This has now been fixed and functions correctly.
Analytical Engine
-
Previously, in some cases, filtering a dashboard or widget (for example orders totaling over 500) did not display filtered or sorted data correctly in the Analytical Engine. As a result, the dashboard and widgets did not display the correct data. This has now been fixed and filters in the AE operate as expected.
Assistant
-
Previously, when clicking Add to Dashboard from the assistant, the widget was not always added to the dashboard. This has now been fixed and works as expected.
Authentication
-
Session Inactivity configuration is now applied to all roles. Previously, changing the configuration for admin roles was not applied and the previous one was used.
Compose SDK Mode
-
An issue was fixed with Sisense Intelligence Forecast that rendered the forecast incorrectly in CSDK and CSDK mode.
Connectors
-
Previously, under certain conditions, a race condition occurred in Snowflake during schema SWAP and DROP operations. This has been fixed and these commands are strictly serialized, ensuring data integrity and preventing accidental schema deletion during high-velocity deployments.
Git
-
Committing large data models to Git now works as expected, as the limit was increased. Previously, attempts to commit very large assets (such as data models with hundreds of tables) would fail and return “PayloadTooLargeError,” blocking Git integration for big projects.
Narrative
-
Previously, self-hosted users could change the narrative provider via API to a provider that is not available for them. This has now been fixed and unavailable providers cannot be designated.
Outer Joins
-
Previously, outer joins in legacy models were being sent as-is in compatibility mode, causing inconsistencies. This has been fixed and when using compatibility mode all joins are automatically converted to inner joins, while preserving the original join types which are restored when switching back to the Analytical Engine (AE).
Reports
-
Previously, when using the “Send me a report now“ option in Report Manager, the system did not add the date and time to the email header. This has been fixed and the email’s header now includes the date and time when the report was generated.
-
Previously, after upgrading Sisense from L2023.6 to L2025.1 (Report Manager 1.11.37), CSV exports were returned in UTF-8 encoding with BOM. This has been fixed and CSV files are now exported in plain UTF-8 without BOM.
Reporting in WAT Flow
-
Changed filters are now reflected in the exported PDF report of the dashboard accessed in the Web Access Token flow. Previously, filters were not applied, creating a discrepancy between the data in the dashboard and the exported PDF file.
Tenants
-
Forgot password emails for tenants now work properly, even if SSO was enabled and later disabled. Previously, if SSO had been enabled for a tenant, users did not receive forgotten password emails, and attempts to reset passwords resulted in errors and no email was sent.
User Parameters
-
Validation for null values has been added when creating user parameters via API - the request is not executed and an error is returned. Previously, the parameters were created and caused issues with editing such parameters in the UI.
User Roles
-
It is now possible to change the role of admin created in the tenant. Previously, this option was blocked with the only remaining option being to delete and re-create the user with the correct role.
-
Previously, in rare circumstances (such as cache expiration during API authentication), the SysAdmin’s role could be reset to a Viewer role, disrupting automation and scheduled tasks. This has now been fixed such that SysAdmin user roles now remain stable and are no longer unexpectedly downgraded to Viewer.
Web Access Token
-
Accessing dashboards via Web Access Token (WAT) in the environment with the New Navigation Bar enabled now works as expected. Previously, the page failed to load with the error
TypeError: Cannot read properties of null (reading 'getLogo')causing issues in corresponding WAT-based solutions.
Widgets
-
After upgrading from 2025.3 to L2025.4.0.109, when a column's data type was configured as Text, empty cells within the table widget would occasionally display as "(blank)". This has been fixed, and the cells now appear empty.
Limitations
SAML SSO in iFrame on Chrome 142+ (Private IP Deployments)
SAML SSO login flows inside an iFrame on Chrome 142+ with Sisense hosted on a private IP are not supported. Once users are authenticated (for example, by logging in outside the iFrame), viewing dashboards in an iFrame is supported.
Workarounds:
-
Perform SAML SSO in the top-level window (outside the iFrame), then load Sisense in the iFrame using the existing session.
-
Alternatively, expose the SAML callback / Sisense endpoint via a public HTTPS hostname (for example, using a reverse proxy or WAF) that forwards traffic to the internal Sisense instance.
2026.1.1 Release Overview
Cloud Availability
This release is currently only available to cloud customers. It will be released shortly for on-premise availability as well. As the content is still in progress, it is recommended that you check back here occasionally for the latest updates.
The content below describes the new features, improvements, and bug fixes included in the February 2026, 2026.1.1 release.
For a list of release dates and Sisense's end of support schedule, see Sisense Version Release and Support Schedule.
For information about the Sisense gradual rollout process, as well as an explanation of how the versions and release notes relate to content added during the rollout, see Sisense Gradual Rollout Process.
What's New
The following table lists the high-level impact (or potential impact, if any) of new features, and how to handle it if upgrading to version 2026.1.1 or newer. Continue reading the Release Notes below the table for a detailed explanation of these features, as well as improvements and fixes.
| Feature | Issues and Actions to Consider |
|---|---|
|
Currently in Beta. |
|
| Outer Joins (Beta) |
Currently in Beta. |
Calculated Dimensions (Beta)
Business Analysts and Dashboard Designers can now create new data grouping and categorization dimensions on-the-fly (e.g., Concat, Left, Right) directly within the widget editor, without requiring backend data modeling changes or ElastiCube rebuilds.
Use the Widget Editor for:
-
Binning & Grouping: Drag-and-drop values into custom groups (e.g., grouping "sku_124" and "sku_124_old" into "sku_124").
-
String Manipulations: Functions to extract parts of text or reshape dates (e.g., LEFT(Region, 3)) to create new axis categories.
Outer Joins (Beta)
Note:
Outer joins are only compatible with the Analytical Engine.
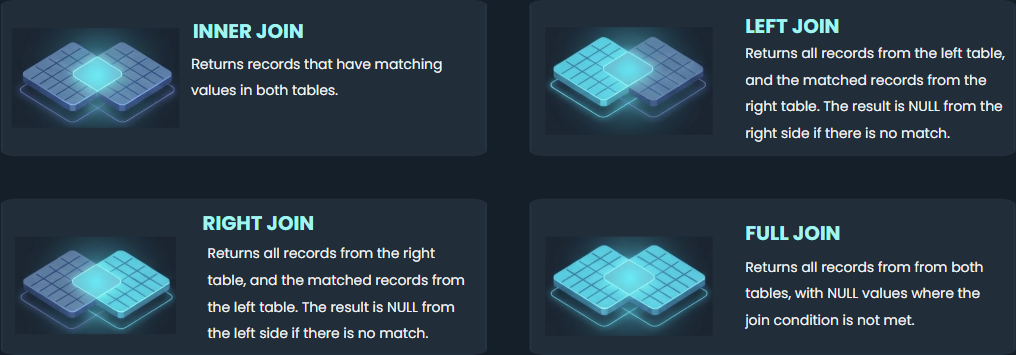
Overview:
Sisense has added support for left, right, and full outer joins in the data modeling environment (for both ElastiCubes and Live Models), moving beyond the current default of inner joins. This allows dashboards to retain unmatched rows, thereby providing more comprehensive analysis, and easier identification of data integrity issues.
Background:
Inner joins remain the default when creating a join between tables. They only show rows with matching data and are faster to execute. However, inner joins exclude partial matches, and thus, prevent potential analysis of missing data such as “customers who haven’t placed any orders” and “unsold products”. Previously, outer join operations were only available via ETL or derived tables. However, this method was not flexible and time-consuming. It also caused data model complications.
The outer joins feature (left, right, and full joins) provides a more comprehensive overview of data, highlighting not only where queries match but also showing non-matching data. Data modelers can execute joins directly within the user interface, minimizing the need to edit SQL or perform other manual operations. The new feature improves data modeler-side controls, thus establishing a stronger emphasis on data governance, as these decisions are made prior to dashboard creation and data analysis.
How it Works:
When editing a relationship between tables in a data model, a drop down menu lists all available join types: Default, Inner Join, Left Join, Right Join, or Full Join.
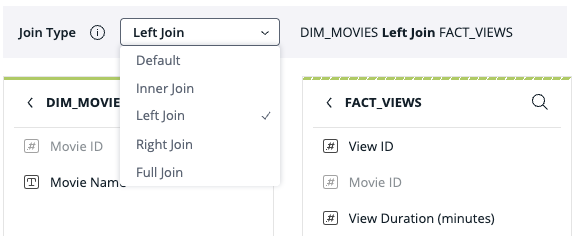
What’s Improved
Installation
-
This change only affects customers who are installing Sisense with SSL (or using gateway port 80).
Due to the approaching ingress-nginx end of life, Sisense has migrated from the old ingress-nginx implementation to the new method of Gateway API - the NGINX Gateway Fabric implementation:
This means that for new customers who choose to install Sisense with HTTPS dns name + SSL (or using gateway port 80), the Helm chart of Nginx Gateway Fabric (NGF) will be installed + a Kubernetes
Gatewaywill be created + a KuberneteshttpRoutewill be created in their namespace (instead of the oldingressas in the past).WARNING:
For existing customers with SSL who have the old
ingress-nginximplementation - the next update will delete the ingress-nginx helm chart and will replace it with the new NGF implementation!If you choose to keep the old
ingress-nginximplementation (EOL March 2026), open the file installer/extra_values/installer/installer-values.yaml and setinstall_nginx_gateway_fabric: false. This will skip the deletion ofingress-nginxand will also skip the installation of NGF, and will continue to use the oldingress(and will not createhttpRoute).For instructions to manually install the Sisense Helm Chart with SSL, see Manually Installing Sisense Helm Chart - with SSL.
Outer Joins
-
The Outer Joins feature is now turned on by default for all existing and new users. To disable or re-enable it, navigate to: Admin > Feature Management > Advanced Analytics > Outer Joins Control.
-
Non-default join types are now highlighted in data models:
-
In list view: for tables with a single join relationship, an icon is displayed in the table row. For tables with multiple join relationships, the icons are displayed in the join details popup.
-
In diagram view: visual indications of non-default join types now appear directly on the relationship lines in the data model graph using Venn diagram-style visuals.
-
-
When selecting a join type, the UI now displays a visual representation of an inner join next to the default join option to indicate the type of join.
-
When creating a join between 2 tables, users can switch which table appears on the left and right sides of the join panel by clicking the button (see screenshot below).
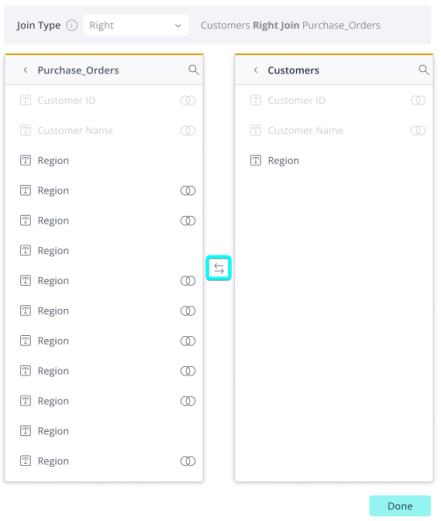
Limitation:
-
When using “Compatible mode” the join type cannot be edited and the corresponding dropdown selector is disabled.
Report Manager
-
In multitenant systems, all tenants can now schedule reports using Report Manager.
Sisense Intelligence
-
Sisense Intelligence features now use GPT 4.1 with the Sisense Managed LLM.
-
The Assistant and Narrative now fully adapt to your selected system language, and are not exclusively in English. This includes generating Narrative content in the selected language and localizing all Assistant menus and tooltips.
-
The NLQ agent for the Assistant has been improved to provide better accuracy, consistency, and stability.
-
Users can create dashboards and add various widgets to the same dashboard within a chat session in the Assistant.
What's Fixed
Analytical Engine (AE)
-
When long column names are used within functions, the AE generates a descriptive alias. If this string exceeds 128 characters, some providers (e.g., MSSQL) reject the query with an error. The row function alias length has now been limited to 128 characters, thereby preventing this error from occurring.
Pulse Alerts
-
Previously, when one user deactivated a Pulse notification, all other users stopped receiving the notification as well. This has now been fixed and Pulse email notifications are only deactivated for the specific user who executed the request.
Reports
-
Previously, in some cases, when dashboard and widget filters were set to different date-level granularities, the UI reflected both filters but reports generated by Report Manager ignored both filters. This has now been fixed and Report Manager adheres to both filters.
Sisense Intelligence
-
Previously, a large amount of tokens was sometimes consumed when calling the available fields tool. This has now been fixed, and fewer tokens are used.
-
For on-prem systems only - previously, in certain circumstances, the Sisense Intelligence admin page sometimes hung. This has been fixed and the page now opens as expected.
-
Previously, sometimes scrolling via the scroll bar in the Assistant chat did not work. This has now been fixed and you can scroll as expected, using either the mouse or the scroll bar.
SSO
-
SSO enablement and configuration is now saved for tenants as expected. Previously, configuration changes were not saved.
Widgets
-
Previously, when a “Break by” field in a line chart contained null or empty value, the chart rendered completely empty and affected relevant dashboards. This has now been fixed and line charts no longer render empty if a “Break by” field contains a null or empty value.