Email-Based Two-Factor Authentication (2FA) for Sisense Native Users (Beta)
Email-based Two-Factor Authentication (2FA) adds an additional layer of security for Sisense users who authenticate with a username and password (native users). When 2FA is enabled, users must enter a one-time verification code sent to their email after successfully entering their credentials.
About Two-Factor Authentication
2FA requires users to provide:
-
Their Sisense username and password
-
A one-time verification code sent to their registered email address.
By requiring both, Sisense significantly reduces the risk of unauthorized access due to password reuse, phishing, or credential theft, which is especially important in distributed and work-from-home environments.
Supported Users and Scenarios
Sisense supports multiple authentication methods:
-
Named (Native) Users: Users created directly in Sisense with a username and password. See Managing Users for more information.
-
SSO/AD Users: Users created and/or authenticated via an external Identity Provider (IdP) using Single Sign-On (SSO) or Active Directory.
-
Web-Access Token: Stateless and volatile access to the analytics via a web access token.
Email-based 2FA applies only to Native Sisense users who sign in with a username and password.
Sisense email 2FA does not apply to externally created and managed users such as SSO or Active Directory (AD) users. These users rely on the MFA/2FA mechanisms provided by the IdP (for example, Okta, OneLogin, Azure AD). Sisense does not add an additional 2FA step for them.
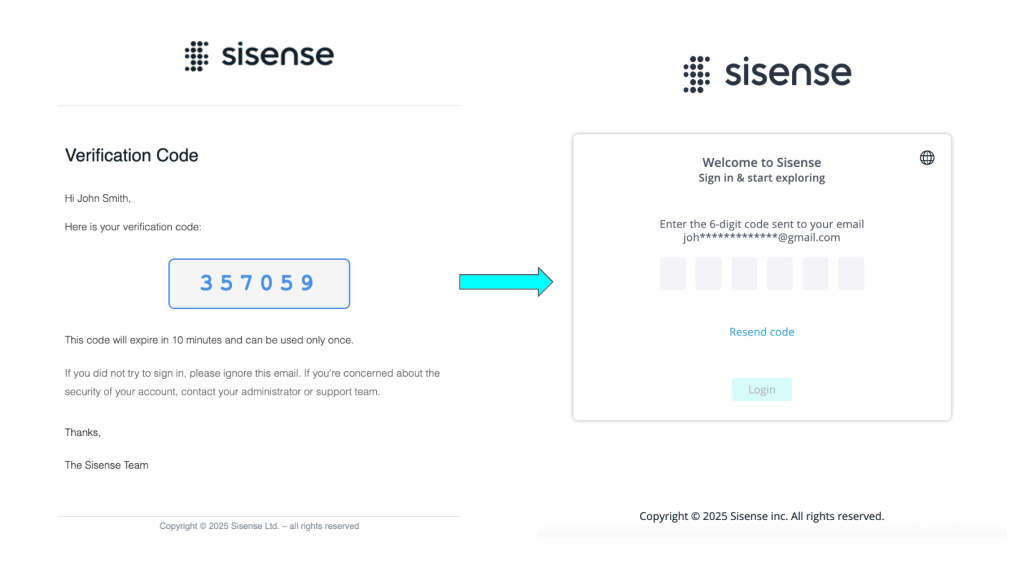
To Sign-in Using 2FA:
-
Navigate to the Sisense login page and enter your username and password. Sisense alerts the user that a one-time password (OTP) will be sent to the user’s email.
-
Enter the OTP you received via email on the 2FA screen. You will be redirected to the application. If the OTP is invalid or expired, you will be redirected to the page you were using when the session expired.
Enabling and Configuring 2FA
2FA is controlled with a cascading combination of the following settings:
-
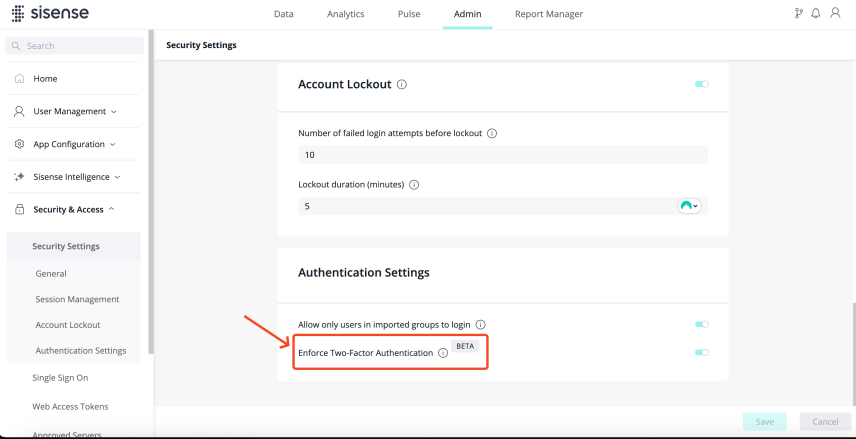
Deployment-wide feature toggle - Controls whether email-based 2FA is active for the entire deployment.
-
Located in: Admin > Security and Access > Security Settings > Authentication Settings > Enforce Two-Factor Authentication.
-
When this toggle is OFF, no users are prompted for 2FA, even if they are configured to require 2FA at the user level.
-
-
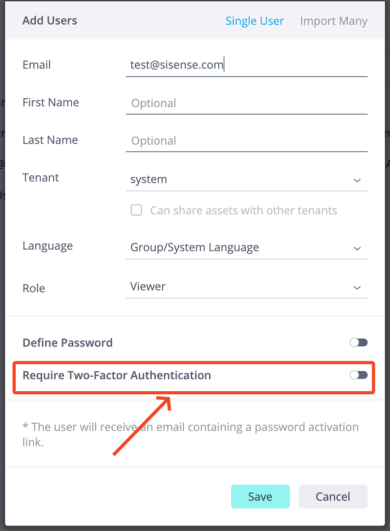
User-level configuration - Specifies whether 2FA should be enforced for a specific native user when 2FA is enabled at the deployment level.
-
In the user object returned by the API, this appears as a Boolean property:
isTwoFactorRequired: true | false. -
2FA is enforced for a user only when both:
-
The deployment-wide feature toggle is ON, and
-
isTwoFactorRequiredfor that user is set to true
-
-
Note:
When the deployment-wide 2FA toggle is OFF, per-user 2FA settings remain visible and editable but have no effect until the global toggle is turned ON.
Turning the 2FA feature toggle ON or OFF does not modify per-user configuration. It only affects whether the per-user setting is enforced at login.
SSO and AD users are always excluded from Sisense’s email 2FA policy. isTwoFactorRequired is always false and cannot be changed.
Administrators can turn off 2FA for specific native users, for example:
-
Synthetic / machine users
-
Integration or automation users
-
QA or test accounts
-
Other accounts where interactive logins are not required or are managed differently
This configuration is independent of the deployment-wide toggle and can be changed at any time.
The following table summarizes the interaction between the deployment-wide feature toggle and the per-user setting:
| Global 2FA Toggle | isTwoFactorRequired | Is 2FA Required at Login? |
|---|---|---|
| OFF | true or false | No (2FA is globally disabled) |
| ON | true | Yes, OTP is required after entering username/password |
| ON | false | No, regular username/password login only |
Turning the global toggle ON after it was OFF will re-activate 2FA for all native users with isTwoFactorRequired: true. Turning it OFF disables 2FA for everyone without changing any per-user settings.
Brute-Force Protection
2FA is integrated into the existing account lockout mechanism to retain the existing protection against brute-force account attacks. Each time the OTP or password is entered incorrectly, the Account Lockout Threshold counter is increased by 1.
The generated OTP expires after the allowed number of attempts is exceeded or when the user requests a new OTP.
Suggested Enablement Flow
To ensure that the authentication email and overall system are configured correctly, Sisense suggests testing 2FA for a small number of users and then enabling the System-Wide 2FA feature toggle. If it is working as expected, user-level 2FA configuration can then be applied to all required native users. Doing this will help ensure users don't experience breaking changes.
Disaster Recovery and Fallback Options
While Sisense does not provide a dedicated recovery flow with reset codes, if a user cannot receive a 2FA code (for example, email issues, incorrect email address, or locked-out users), the following recovery options are available:
-
Temporarily toggle off 2FA at the deployment level. Once the issue is resolved, re-enable the global 2FA toggle to restore protection.
-
An admin can disable 2FA for affected native users. This allows the user to log in using only a username and password.
On-Premises Deployments
Email-based 2FA is supported for Sisense on-prem deployments, with the following requirements:
-
Correct configuration of email (SMTP) is required (system must be able to send email).
-
Outbound connectivity to your email infrastructure must be available.
-
Local security, backup, and disaster recovery processes must include 2FA configuration and logs as relevant.
Multitenancy
2FA settings are applied to all users created in custom tenants (see Sisense Multitenancy), in the same manner that they are applied to system tenants. Please note that 2FA cannot be enabled or disabled for an individual tenant.
Beta and GA Scope
Due to the sensitive nature of authentication, 2FA will initially only be available in beta. This requires users to manually enable user-level 2FA configuration.
An admin can enable/disable 2FA via Admin > Users > Edit User or via the 1.0 PATCH users/bulk.
Sample payload:
[
{ "_id": "6947cd61fe7edd7d5ec1927a", "requireTwoFactorAuth": true },
{ "_id": "6947cd61fe7edd7d5ec1927b", "requireTwoFactorAuth": true },
{ "_id": "6947cd61fe7edd7d5ec1927c", "requireTwoFactorAuth": true },
{ "_id": "6947cd61fe7edd7d5ec1927d", "requireTwoFactorAuth": true },
{ "_id": "6947cd61fe7edd7d5ec1927e", "requireTwoFactorAuth": true }
....
]When 2FA becomes GA, Sisense will add the ability to bulk edit user-level 2FA configuration from Admin > Users, and 2FA will be enabled by default for those users that have not had it specifically set it by admin previously.
Deployment-wide 2FA will remain OFF to prevent any breaking changes at this stage. Once the feature is GA, Sisense will define a timeframe for gradual 2FA enablement for all human users.
Limitations
-
Current Two-Factor Authentication does not support ‘Session Inactivity' - the second step will not be triggered and the user will get access to the application after the login/password login step.