Sisense Multitenancy
Sisense supports multitenancy in several different ways:
-
Self contained - Built-in application based multitenancy with full isolation between tenants
-
Multi-instance - Installation based multitenancy with different tenants on separate servers
-
Internal capabilities - Multitenancy based on Sisense application features and user groups
The best approach for you depends on your requirements, preferences and available resources.
Note:
Multitenancy is not available for SaaS customers.
Self-contained Multitenancy
Sisense self-contained multitenancy adds a hierarchy to user management to support multiple organization tenants (or multiple environments) in parallel on a single Sisense deployment. This multitenancy is application based and provides a complete separation between tenants.
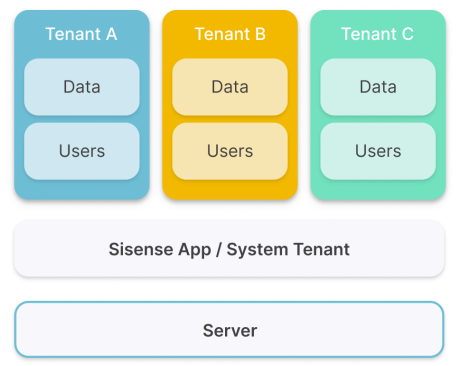
Advantages of Sisense self-contained multitenancy:
-
Security:
-
Highly secure application based multitenancy prevents data leaks between tenants
-
Auditing and logging capabilities on a per-tenant basis
-
-
Operational Efficiency:
-
Due to the high level of security, tenant admins can handle administrative responsibilities for their own tenant
-
Maintenance processes are more efficient, such as adding new tenants, new users, and handling system upgrades
-
-
Improved Control:
-
System admin has clear visibility of organization tenants, including the number of tenant users and dashboards
-
Supports customized tenant functionality, such as user management and feature management, (including SSO and white labeling)
-
See Self-contained Multitenancy and Managing Self-contained Tenants to learn more about Sisense self-contained multitenancy.
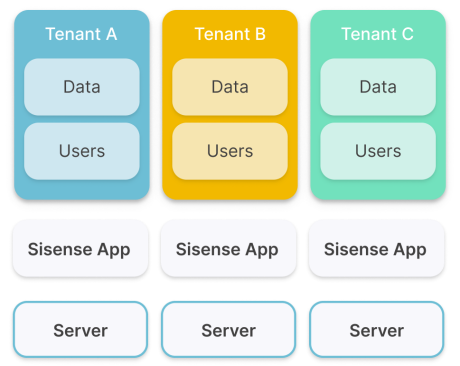
Multi-instance Multitenancy
With multi-instance (installation based) multitenancy, completely separate Sisense deployments run for different tenants on separate servers.
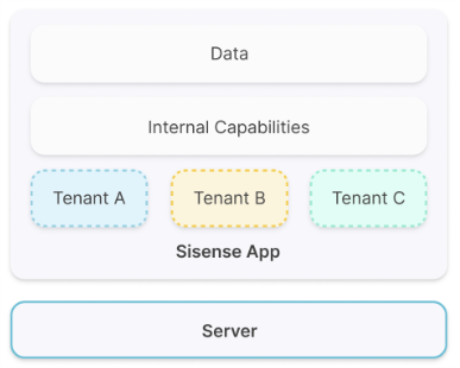
Internal Capabilities Based Multitenancy
Internal capabilities (implementation) based multitenancy is frequently used for OEM deployments. In this approach the segregation between tenants is achieved using a combination of the Sisense application features and user groups.
A common example of this type of multitenancy uses shared data models, and dashboards with row-based security.
See OEM Architecture for more information about this and several of its related approaches to multitenancy.
Tenant Segregation Level Comparison
This table compares, based on the type of multitenancy, the degree to which tenants are isolated from each other and to what degree they share various types of functionality.
|
Multi-instance Multitenancy (installation based) |
Self-contained Multitenancy (application based) |
Internal Capabilities Multitenancy (user group and implementation based) |
|
|---|---|---|---|
|
User Isolation Level: |
Isolated user management per deployment |
Isolated user management per tenant |
All users login using the same URL |
|
User Authentication: |
Dedicated SSO per deployment |
Dedicated SSO per tenant |
Single SSO / SSO router add-on shared by all tenants |
|
Data Access: |
Tenants can create data models and dashboards that are private to them |
Tenants can create data models and dashboards that are private to them |
Tenants can create dashboards but don’t have access to the data model |
|
Branding: |
White labeling per deployment |
White labeling per tenant |
Same white labeling configuration shared by all tenants |
|
Computer Resource Isolation: |
Full isolation |
Isolation using Data Groups |
Isolation using Data Groups |