Cloud Platform
The Sisense cloud product and all data are hosted on industry-leading cloud provider Amazon Web Services (AWS).
Cloud Hosting Architecture
Sisense uses Amazon Web Services (AWS) as a cloud service provider and its highly available data center facilities in multiple regions worldwide.
Our cloud infrastructure is powered by AWS Managed Kubernetes Service (EKS) or dedicated EC2 instances, ensuring that each customer receives a fully isolated cluster within their own dedicated VPC.
-
Infrastructure as Code (IaC): Terraform is used to provision and manage the cloud infrastructure.
-
Deployment Management: Helm is used for Sisense application deployment and configuration.
Operating System
Sisense Cloud single-node runs on Ubuntu, and Sisense Cloud EKS (multi-node) runs on Amazon Linux, ensuring security, performance, and seamless integration with AWS services. We continuously certify and upgrade the Linux version to leverage the latest security patches, performance improvements, and feature enhancements, ensuring a secure and optimized environment.
Architecture & Scaling
Sisense Cloud supports both single-node and multi-node architectures, depending on the customer's requirements.
Autoscaling
-
Horizontal Pod Autoscaler (HPA): Enabled for automatic scaling based on workload. Sisense continuously monitors performance and fine-tunes autoscaling configurations to ensure optimal resource utilization, efficiency, and responsiveness to varying demands.
-
Vertical Pod Autoscaler (VPA): Planned for future implementation.
Load Balancing & Traffic Management
Load balancers are placed in front of each deployment to distribute traffic efficiently and ensure reliability.
High Availability & Fault Tolerance
-
High availability is ensured through AWS availability zones and robust failover mechanisms.
-
There is currently no multi-region redundancy support.
Region Availability
Sisense Cloud can be deployed in any of the following supported AWS regions of the customer's choice:
-
af-south-1
-
ap-south-1
-
eu-west-3
-
eu-west-2
-
eu-west-1
-
ap-northeast-2
-
ap-northeast-1
-
ca-central-1
-
ap-southeast-1
-
ap-southeast-2
-
eu-central-1
-
us-east-1
-
us-east-2
-
us-west-2
Customer Isolation & Security
Each customer has a fully dedicated and isolated environment, ensuring data security and compliance:
-
Own VPC per customer.
-
Dedicated Kubernetes cluster per customer.
-
Dedicated compute resources to avoid resource contention.
-
Strict network policies and IAM controls to prevent cross-customer data access.
Scalability Options
-
Customers cannot independently scale compute or storage resources.
-
Scaling requires a request to Sisense Support, as it may impact licensing costs.
-
All instances follow predefined instance sizes.
Logging & Monitoring
-
Monitoring: Prometheus is used for system and application monitoring. Sisense deployment contains predefined Grafana dashboards for self-monitoring.
-
Logging: Fluentd is used for log aggregation.
Note: Logs are stored for 1 month.
-
Customer Access to Logs: Combined logs are accessible in the admin page.
-
Log Export: External log shipping (e.g., to Datadog) is not supported at this time.
Audit Logs
Sisense Cloud provides built-in audit logs for security and compliance purposes. More details can be found in our documentation: Sisense Audit Logs.
Data Backup and Restore Policy
Sisense is responsible for performing regular backups of customer data and restoring that data when required, in response to various incident scenarios. The following outlines Sisense’s backup and recovery practices, including retention policies, Recovery Time Objective (RTO), and Recovery Point Objective (RPO).
Repository Backups
Sisense performs backups of both file systems and application metadata in accordance with the following practices. Backups are executed at midnight (based on regional time zones) and prior to system upgrades.
|
Category |
Backup Practice |
Retention |
|
File Systems |
Nightly snapshots are taken of all disk volumes (excluding the root partition). Snapshots follow the time zone of the hosting server. |
Daily - Snapshots for the current day and the previous day Weekly - One snapshot every weekend, retained for the prior 4 weeks Upgrade - Snapshot taken before each upgrade, retained for 14 days |
|
Metadata |
Sisense performs nightly backups of application metadata. Restoration may require rebuilding all cubes. |
Daily - Backups for the last 7 consecutive nights Weekly - One backup every weekend, retained for the prior 4 weeks |
Security and Disaster Recovery
-
All backups are encrypted at rest to ensure data confidentiality and integrity.
-
Backups are available for restoration as required during the active subscription term.
-
At subscription termination, a final backup is retained for 30 days post-termination.
Recovery Objectives
-
Recovery Point Objective (RPO): Sisense’s RPO is 24 hours, meaning that in the event of an incident, data can be restored to the state of the last successful backup (nightly).
-
Recovery Time Objective (RTO): Sisense’s RTO is up to 1 hour, depending on the nature and scale of the incident, with the goal of restoring services and data access as quickly as possible.
Access to the Cloud Environment
How your users access the environment is described in the diagram below.
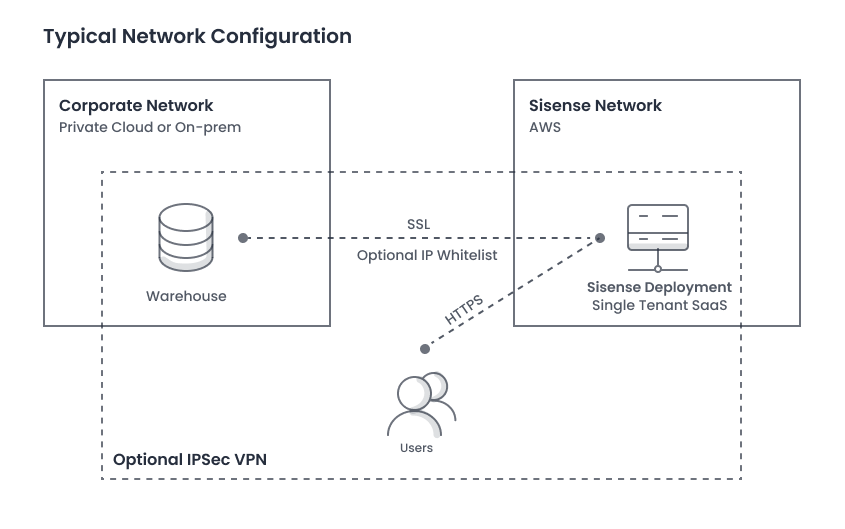
From inside or outside your network, users connect to your dedicated Sisense deployment, hosted on AWS. Connections are secured with HTTPS and connections to and from your databases can be secured by IPSec VPN, VPC Peering, Private link, Transit gateway, or SSH Tunneling, depending on your infrastructure.