Implementing Amazon EBS CSI Driver for GP3 Volumes
If you use Kubernetes on Amazon EKS v1.23 or higher with Amazon FSX or EFS, see Creating a Service Account for the EBS CSI Driver on EKS.
If you want to install the EBS CSI driver and do not use Amazon EKS v1.23 (or higher) with FSX or EFS, then follow the directions below to create an EBS CSI policy.
Although it is possible to work with in-tree storage drivers, the optimal solution is to use the EBS Container Storage Interface (CSI) driver. This method requires you to give the Kubernetes nodes permission to modify EBS volumes. With this configuration, the CSI driver will automatically supply the EBS disks Sisense needs, or remove the disks if you decide to delete Sisense.
Note:
Migration from an already existing Sisense installation is not supported with this implementation of the EBS CSI
driver.
First, you need to create an EBS CSI policy. Then, you can attach the new policy to the Sisense node
groups. Finally, you edit the Sisense installer-values.yaml file to enable the EBS CSI driver in Sisense.
To create an EBS CSI policy:
- Log in to the AWS Management Console and open the IAM console at https://console.aws.amazon.com/iam/.
- In the navigation pane on the left, select Policies.
- Select Create policy.
-
Choose the JSON tab and enter the following JSON policy:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "ec2:AttachVolume", "ec2:CreateSnapshot", "ec2:CreateTags", "ec2:CreateVolume", "ec2:DeleteSnapshot", "ec2:DeleteTags", "ec2:DeleteVolume", "ec2:DescribeAvailabilityZones", "ec2:DescribeInstances", "ec2:DescribeSnapshots", "ec2:DescribeTags", "ec2:DescribeVolumes", "ec2:DescribeVolumesModifications", "ec2:DetachVolume", "ec2:ModifyVolume" ], "Resource": "*" } ] }For details about the IAM policy language, see IAM JSON policy reference.
- Choose Review policy and the Policy Validator reports any syntax errors.
- On the Review policy page, enter a Name and an (optional) Description for the policy. It is recommended that the policy name include EBS_CSI so it can be easily identified in the future.
- Review the policy Summary to see the permissions that are granted by this new policy.
- Choose Create policy to save the policy.
To attach the EBS CSI policy to a cluster:
-
After the policy is created, open the Amazon EKS console at https://console.aws.amazon.com/eks/home#/clusters.
-
Choose Clusters, and select the target cluster from the list.
.png)
-
In the cluster information, select the Configuration tab and then the Compute tab.
-
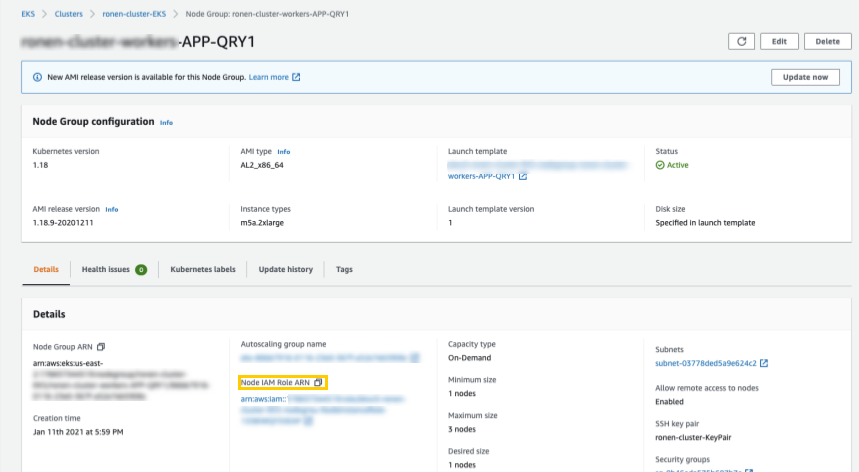
Select a Node Group from the Group Name list. You will attach the new policy to this node group so it can use the EBS CSI plugin. Eventually, you will attach the new policy to all of the node groups in this cluster.
-
Select the link under Node IAM role ARN to open the role configuration console.
-
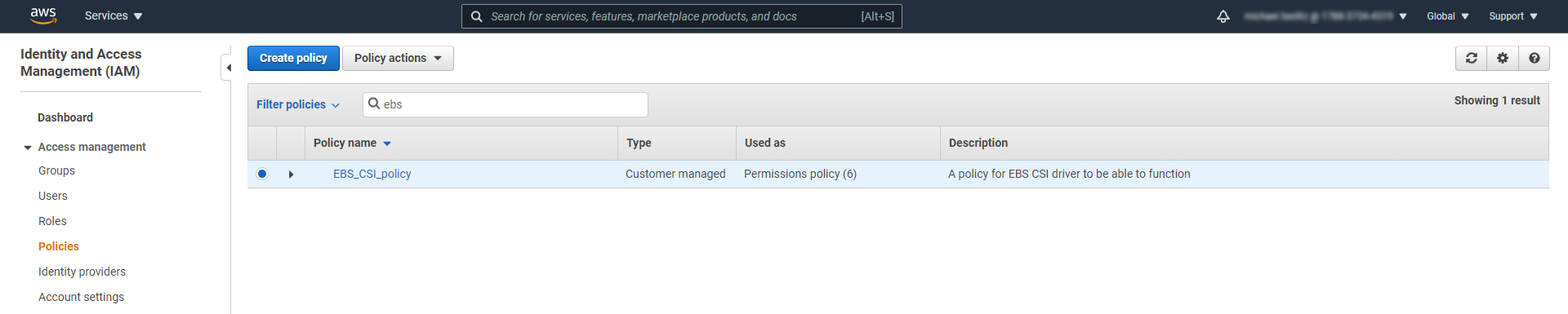
Click Attach policies and in the Attach Permissions Search field enter the EBS policy name that you created .
-
Select the policy from the list and click Attach policy.
-
Repeat steps 4-7 for the remaining Node Groups in your cluster.
To enable the EBS CSI driver in Sisense:
-
Open the yaml file
vim installer/extra_values/installer -
Go to the ebs_csi section in the YAML file and set the enabled parameter to true.
enabled: true - Save the changes to the YAML file and continue with the Deploying Sisense on Amazon EKS procedure.
To enable EBS CSI using Helm Provisioner:
Use the following syntax to apply the installer-values.yaml file which you can extract from the generic installer tarball:
helm install prov-sisense $CHART_URL \ --namespace=$NAMESPACE \ --create-namespace \ --set-file installer_values=./installer-values.yaml