Cloud Connectivity
Sisense Cloud Connectivity - Secured DB Network Connections
To connect to your DB (SQL Server, Oracle, Redshift, AD, etc.) you must choose one of our supported secure data transfer solutions:
- Direct Connection to Database - With or without SSL. Provide public/external IP of the database.
- Site-to-Site VPN (S2S) (IPSec) - Firewall configuration is required. Access to the database is via internal IP routing.
- SSH Tunnel - SSH tunnel to the SSH server set up on the database server or bastion gateway.
- AWS VPC Peering - For a database deployed on AWS VPC.
- Private Link - For establishing a connection from a Sisense endpoint to a customer endpoint via a private link.
To assist you in this selection, this article contains further detailed information about each below. Once you decide which solution you want to implement, open a ticket so that we can establish the connection.
Direct Connection to Database
Direct Connection to DB opens the DB connection for incoming traffic coming only from the Sisense server IP using external IPs. Some of the DBs also support SSL communication (Direct Connection to Database can be implemented with or without SSL), as referred to in the Data Connectors page.
You must provide Sisense with the following information in order for us to create a Direct Connection to the DB:
- Database public/external IP and port - Direct access requires the public/external IP & Port. If SSL encryption is required, you must create an SSL certificate and forward it to Sisense.
Site-to-Site VPN (S2S) (IPSec)
S2S VPN connection is a secure network method which connects between FW gateways.
The following document describes how the AWS S2S VPN works:
https://docs.aws.amazon.com/vpn/latest/s2svpn/how_it_works.html
The Sisense Cloud team will generate a dual-tunnel AWS VPN gateway. Firewall configuration is required. You will configure the firewall based on the AWS configuration instructions sent to you.
You must provide Sisense with the following information in order for us to create a S2S VPN:
- Firewall model and version
- External firewall IP
- Internal subnet (CIDR format)
- DB(s) IP and Port
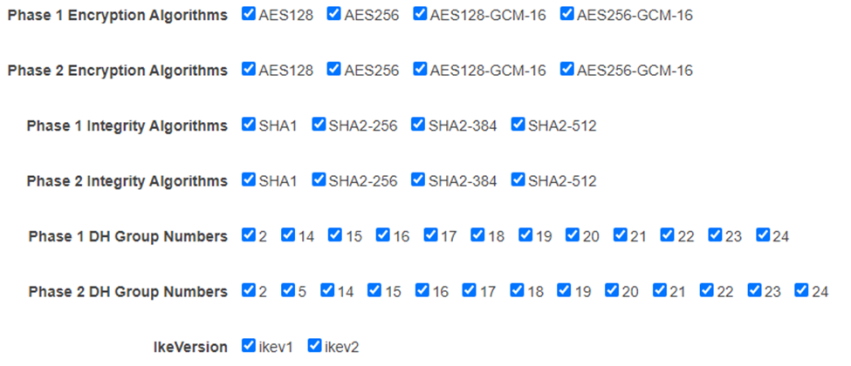
- Encryption - AWS VPN only supports the following:
The following are example configurations for static routing: https://docs.aws.amazon.com/vpn/latest/s2svpn/cgw-static-routing-examples.html
The following are example configurations for dynamic routing (BGP): https://docs.aws.amazon.com/vpn/latest/s2svpn/cgw-dynamic-routing-examples.html
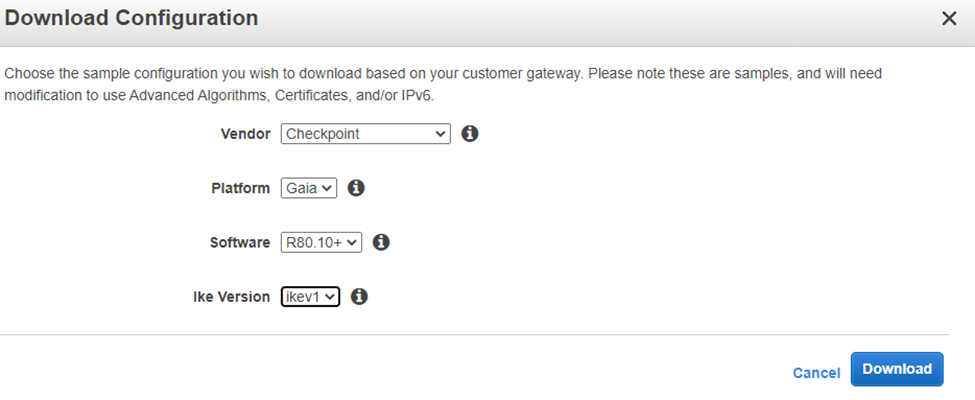
After we set up the S2S VPN connection on AWS, we will send you the details from the AWS configuration file according to your FW Model and Version with IKEV1 or IKEV2 (depending on the AWS available configuration file).
Note:
The only mandatory details are the Tunnel IP and the Pre-Shared-Key.
The encryptions depicted below are samples; you can work with the AWS VPN supported encryptions mentioned above.
SSH Tunnel
You will set up the SSH server on your database server or provide SSH bastion details for the SSH channel. Sisense will work with you on configuration.
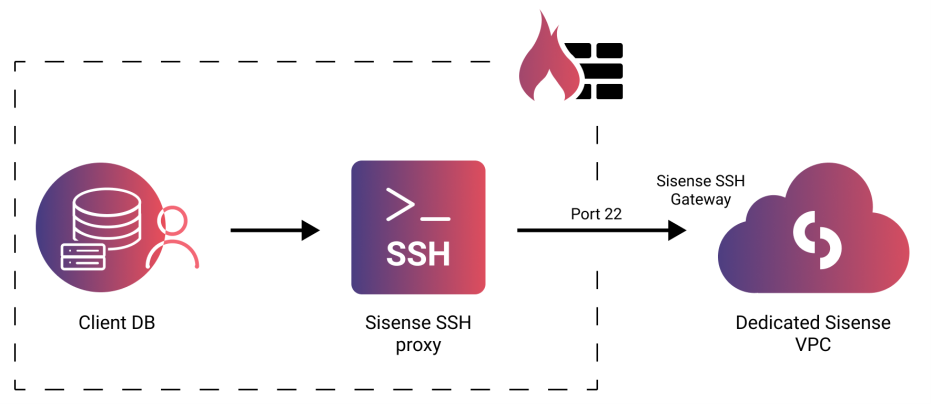
- Create an SSH server within your firewall to enable connectivity and routing to your database.
- After setting up the SSH server, provide Sisense with the following information via a support ticket. This will be routed to the cloud team:
- Bastion / SSH server IP or Domain
- Bastion / SSH server user
- Bastion / SSH port (default: 22)
- Database IP / Domain
- Database port
- In Admin, search for and select Feature Management, which is located under App Configuration, and enable File Management.
- The cloud team will process the request and provide a public key in:
https://<domain>/app/explore/files/custom-certificates/ssh/id_rsa.pub
Connection information will be stored in:
https://<domain>/app/explore/files/custom-certificates/ssh/ssh.config - Add the public id_rsa.pub key to your .ssh/authorized_host file on your SSH server.
Once the above steps are completed, you will be able to connect to your database using the IP and port provided in the ssh.config file.
AWS VPC Peering
AWS VPC peering connection is an interconnection method between VPCs. VPC peering can be established between different regions and accounts.
The following document describes what VPC peering is: https://docs.aws.amazon.com/vpc/latest/peering/what-is-vpc-peering.html
You must provide Sisense with the following information in order for us to create a VPC peering connection:
- AWS Account Number - How to find your account ID.
- Region - Which region your data source is hosted on.
- VPC ID - The VPC ID where your data source is hosted.
- VPC CIDR - Make sure that both ends have different CIDRs so that there will not be an IP collision. If they are the same, the VPC peering connection will fail and will not be established.
- DB IP/URL and Port - The IP or the endpoint URL of the data source and port to test the
connection from the machine using the telnet command.
For example:
telnet mysql-instance1.123456789012.us-east-1.rds.amazonaws.com 3306
The following is an explanation on how to establish a VPC peering connection: https://docs.aws.amazon.com/vpc/latest/peering/create-vpc-peering-connection.html
Private Link
This connection can be used to create a private link from a Sisense endpoint to your endpoint.
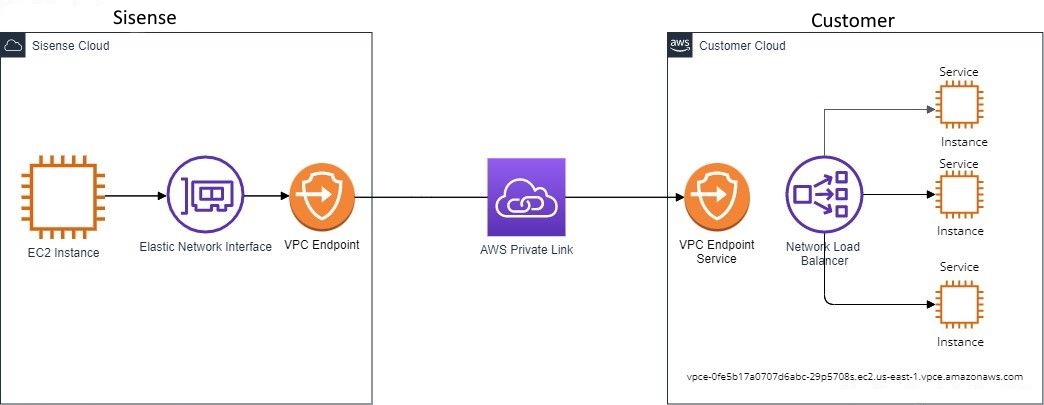
You must perform the following in order for us to connect to your Endpoint Service to establish a Private Link connection:
- Allow Sisense to reach your endpoint service name by adding the Sisense account number in the Allow principals tab.
- Send Sisense the Endpoint Service Name. For example: com.amazonaws.vpce.us-east-1.vpce-svc-123456789123456456789
After Sisense verifies the Endpoint Service Name, we will test the connectivity to your data source.